Introduction to Cybersecurity
Section outline
-
Learning Outcome
MODUL 1:
MODUL 2: Demonstrate a clear understanding of the roles and characteristics of attackers and hackers by distinguishing their intent, legality, and behavior in cybersecurity contexts.
MODUL 3: Describe how each threat can affect systems or data.
-
Cyber Actors: Who’s Behind the Attacks?
-
Definition of hacker vs attacker
-
Types of hackers: White Hat, Black Hat, Grey Hat, Blue Hat, Green Hat, Red Hat
-
Types of attackers: Cybercriminals, Hacktivists, Script Kiddies, Insiders, Nation-state attackers
-
Common motivations: financial gain, ideology, revenge, fame
Hackers Video: Types of Hackers (Hats) Explained
https://www.youtube.com/watch?app=desktop&v=Q0F-pv-n_lc&feature=youtu.be (5:51)
-
-
“Every threat has a story — and it starts with understanding where danger comes from.”
In this module, you’ll discover:
🕵️♂️ Where threats come from – whether from inside the organization or outside it.
💣 How attacks are classified – from passive spying to active disruptions.
⚡ Different types of attacks – like Reconnaissance, Access, DoS/DDoS, and Malicious Code.-
“A source of security threat is the spark before the fire.”
🔥 It’s where the risk starts — from careless users to malicious hackers, everything begins here.
-
“A security attack is when the threat strikes — the danger becomes real.”
🚨 It’s the actual attempt to break, steal or damage your system.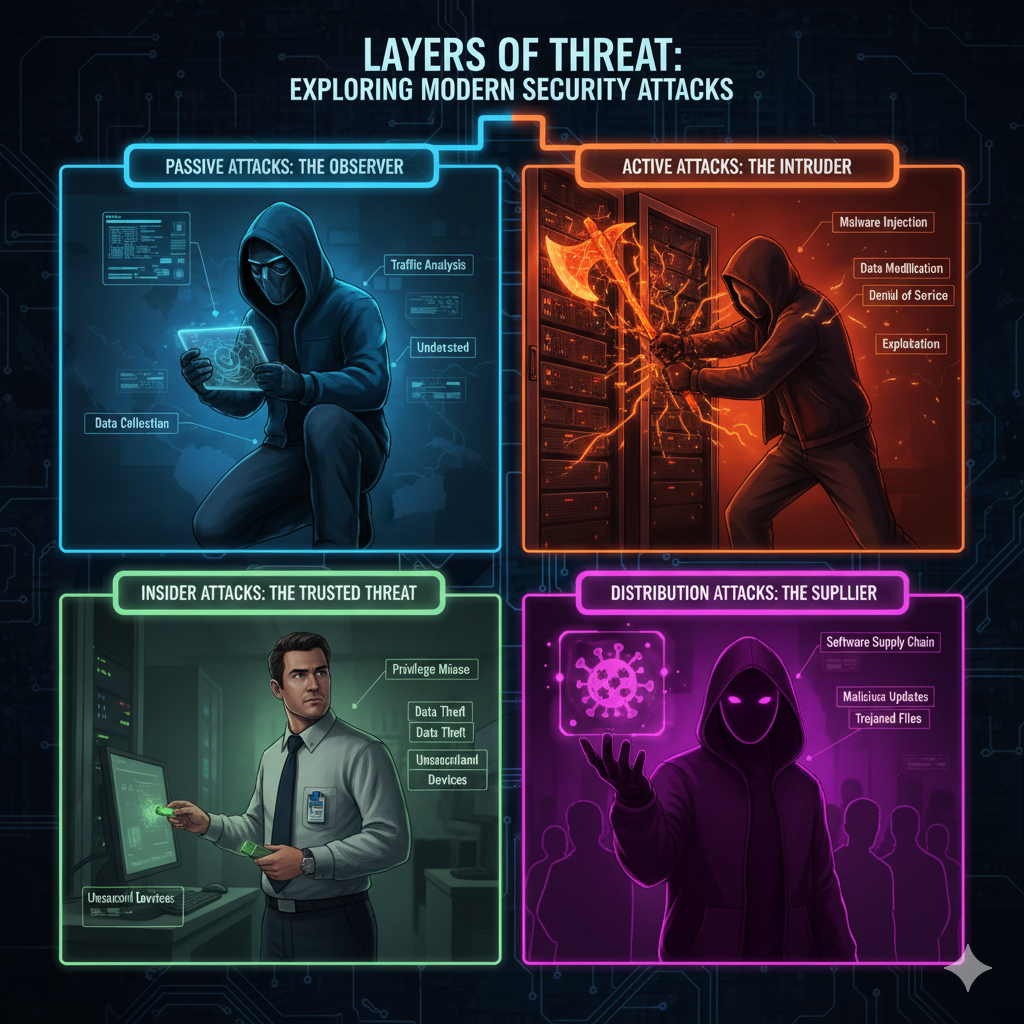
-
“Every attack tells a story — reconnaissance, access, chaos, and code.”
💻 Whether it’s silent observation or total system takedown, the attacker’s mission is simple:
to find a way in before you notice.
-







